3. The following are motivation for DoS and DDoS Attacks: Distraction Damage reputation Hacktivism Fun Profit
4. Type of attacks
Volumetric attacks block traffic by taking up all available bandwidth between the target and the Internet.
Fragmentation attacks target a system’s ability to reassemble fragmented packets.
Amplification attacks exploit vulnerabilities in protocols and broadcast networks. The name is derived from the idea that the attacker uses intermediary computers and networks to amplify the impact of their attack.
Phlashing, also known as bricking, involves pushing incorrect updates to a system’s firmware, causing irreversible damage and rendering the device about as useful as a brick.
5. Tools to create botnets
Botnets are typically used to carryout DoS and DDoS attacks. You can use the following tools to create botnets:
- Shark
- PlugBot
- Poison Ivy
Trin00 is a set of programs used for DoS attacks.
Jolt2 is a DoS tool that sends numerous fragmented packets to a Windows machine.
Targa is a multifunctional tool that can execute WinNuke and teardrop attacks.
Low Orbit Ion Cannon (LOIC) is a free and easy to use DoS tool.
6. DoS Attack Types
A Fraggle attack is a DoS attack that targets UDP protocol weaknesses. A large number of UDP packets from a spoofed IP address are broadcast to a network in an attempt to flood the target computer.
A Smurf attack is a DoS attack that targets ICMP protocol weaknesses.
A SYN flood exploits the TCP three-way handshake. An attacker creates SYN packets with a non-existent source address. When the target machine responds with a SYN-ACK, it goes to the non-existent address, causing the target machine to wait for a response that they will never get.
A Teardrop attack prevents TCP/IP packets from being reassembled. This is done by setting the flags on all frames to indicate that they are fragments and providing instructions to connect to another frame that doesn’t actually exist.
7. Ping command options
ping -n defines the number of echo requests to send.
ping -a is used to resolve adresses to hostnames.
ping -l is used to send the buffer size.
ping -f is used to set the don’t fragment flag in packet.
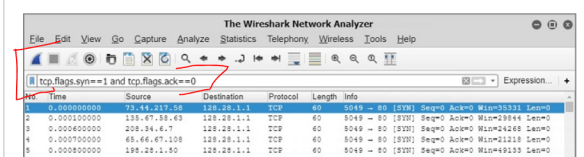
8. Detecting a DDoS attack with Wireshark
The captured and filtered packets show many SYN packets being sent from many different sources, but all destined for the same target or destination address. This is a strong indication that a DDoS attack is currently happening.
Whether they are legitimate or created by a hacker, SYN packets have a hex value of 0x002.
Since a DDoS flood is happening, there isn’t time or bandwidth available to see many (if any) matching SYN-ACK packets.
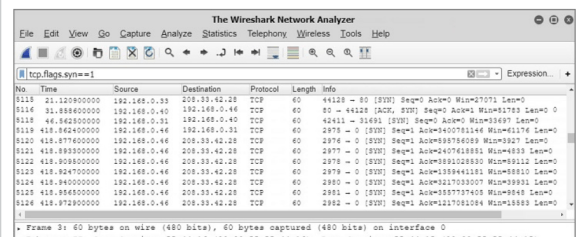
9. Detecting an ICMP flood with Wireshark
In comparison to the occasional ICMP ping requests that can be seen on a network, when an ICMP flood attack is happening, the ICMP packets are sent in quick succession from the same source IP address.
As a result, there is little bandwidth available to receive many (if any) ACK or SYN packets. As can be seen from the packets captured, normal ICMP packets can come from different source addresses, such as 192.168.0.33 and 192.168.0.31.
The ping command will send 4 by default if -n isn’t used.
11. Which best describes a reverse proxy method for protecting a system from a DoS attack?
When a DoS attack occurs and a proxy server takes the impact, this is known as a Reverse Proxy DoS protection method. This method redirects all traffic to the reverse proxy before it is forwarded to the real server.
Creating an area of the network called a black hole, where offending traffic is forwarded and dropped, is another attack protection method called Black Hole Filtering. Enabling router throttling can limit the potential impact of a DoS attack and can provide a bit of additional time for administrators to respond to an attack.
Adding extra services, such as load balancing and excess bandwidth, can help provide too many platforms for the attacker to be able to flood. This method is called absorbing the attack.
12. Creating an area of the network where offending traffic is forwarded and dropped is known as what?
Black hole filtering creates an area of the network called a black hole where offending traffic is forwarded and dropped.
Router throttling limits the potential impact of a DoS attack and can provide a bit of additional time for administrators to respond to an attack.
All traffic is redirected to the reverse proxy before being forwarded to the real server. In the event of an attack, the proxy takes the impact.
Anti-spoofing measures ensure that spoofed packets are unable to infiltrate your network.
14. Which of the following best describes the response you should take for a service degradation?
To respond to a service degradation, services can be set to throttle or even shut down in the event of an attack.
You should have more than one upstream connection to use as a failover in the event of a flooding attack.
To absorb an attack, add extra services such as load balancing and excess bandwidth so that you have too much on your network for the attacker to execute a flood attack.
Your response plan should include a checklist of all the threat assessment tools and hardware protections that you have in place.