2. ¿Qué es Zero Trust? | Zero Trust Security: Una guía empresarial (oreilly.com)
Category Archives: AllPosts
Producing Screencast Videos on a PC – LinkedInLearning
Do you need to create a tutorial, a website walk-through, or a business presentation? How do you make sure it’s high quality and easy to view? It’s increasingly important to be able to show people what you’re doing on a computer screen. In this course, instructor Richard Harrington steps through the entire process of producing screencast videos on a PC, from planning and production to editing and output. Richard begins with an overview of what a screencast is and reasons you might need to create one. He explains the gear you’ll need to create screencasts with great production values and shows you how to get ready for your screencast by cleaning up your desktop, setting resolution and audio to optimal levels, and more. Richard presents several recommended tools for recording your screen. He goes over planning, recording, and editing your screencast, then shows you how to export it for different delivery methods.
What Happened to Facebook, Instagram, & WhatsApp?
Several different domain registration companies today listed the domain Facebook.com as up for sale. This happened thanks to automated systems that look for registered domains which appear to be expired, abandoned or recently vacated. There was never any reason to believe Facebook.com would actually be sold as a result, but it’s fun to consider how many billions of dollars it could fetch on the open market.
https://krebsonsecurity.com/2021/10/what-happened-to-facebook-instagram-whatsapp/
NIST Special Publication 800-207 – Zero Trust Architecture
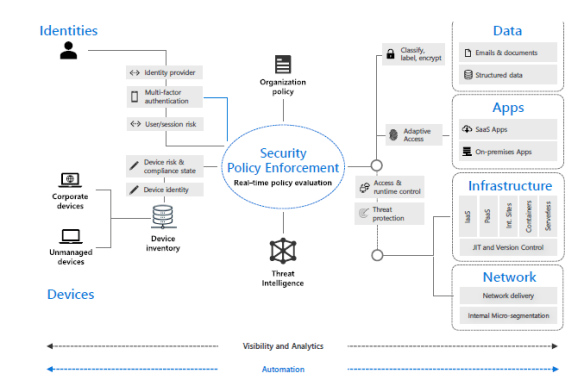
A typical enterprise’s infrastructure has grown increasingly complex. A single enterprise may operate several internal networks, remote offices with their own local infrastructure, remote and/or mobile individuals, and cloud services. This complexity has outstripped legacy methods of perimeter-based network security as there is no single, easily identified perimeter for the enterprise. Perimeter-based network security has also been shown to be insufficient since once attackers breach the perimeter, further lateral movement is unhindered
Making Zero Trust Real with Active Directory
SC-300 part 1: Implement an identity management solution
Roadmap to Zero Trust according to Microsoft
Today’s cloud-based enterprise environments and always-on workforces require access to applications and resources that exist beyond the traditional boundaries of corporate networks, restrictive network firewalls and VPNs. Organizations are moving to modern, more holistic systems of verification to manage enterprise security and to combat threats differently.
Microsoft has adopted a modern approach to security called “Zero Trust,” which is based on the principle: never trust, always verify. This security approach protects our company and our customers by managing and granting access based on the continual verification of identities, devices and services. In this content suite, the Microsoft Digital team shares their strategic approach, best practices, and hands-on learning from our enterprise-wide transition to Zero Trust architecture.